Leonovus gives you control of the security of your data. Leonovus Vault applies data-centric security controls to your data wherever it resides, and ensure security during data migration to other storage infrastructure or cloud providers. You manage all security policies centrally using the intuitive Leonovus Administration web portal.
FEATURES
Encryption with Enterprise-Controlled Keys:
A unique key is generated for each file and encryption is performed using a FIPS 140-2-compliant cryptographic module.
As a foundation, Vault performs AES-256 encryption as it receives data, ensuring that none is stored in the clear. Each data object is encrypted with unique keys using a FIPS 140-2-compliant cryptographic module. You choose how keys are managed:
- If your applications perform encryption, you can disable Vault’s encryption for the storage pools they use.
- If your applications manage keys, but do not perform encryption, applications can pass keys to Vault via its S3-compatible API. Vault will use keys provided by the application to encrypt the files on upload and decrypt them on download. Vault will not store keys.
- If your applications do not perform encryption or key management, Vault will create a unique key for each file and store it in the Vault secure database.
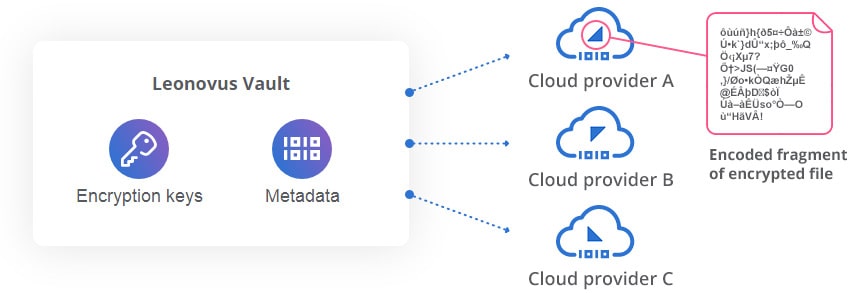
Cloud RAID
With its Cloud RAID feature, Vault goes far beyond basic encryption. Cloud RAID increases data security using erasure coding. Cloud RAID creates redundant fragments of each encrypted data object and distributes the fragments across multiple storage providers. In the event of a compromise, only encoded fragments of encrypted data can be retrieved. Original files cannot be reconstructed. Furthermore, this approach guarantees that your data is completely protected from cloud service provider administrators and extra-jurisdictional subpoenas or data requests, helping you establish true data sovereignty.
Enhanced Data Integrity
Both Vault and Smart Filer monitor the integrity of all data they store by calculating and storing a SHA-256 hash for every file. When a file is retrieved, its SHA-256 hash confirms the file has not been corrupted. Vault also generates and confirms hashes for every fragment created for each file.
